Introduction: The Human Gateway to the Digital World
While routers, cables, and firewalls form the skeletal framework of networks, it’s the application layer—the topmost tier of the OSI model—that translates binary code into human experiences. Every email sent, video streamed, or file downloaded hinges on this layer’s ability to bridge abstract data and tangible user needs. Yet, its role often goes unnoticed, overshadowed by discussions about bandwidth and encryption. This article demystifies the application layer, exploring its functions, real-world implementations, and why it’s the unsung hero powering today’s most transformative network solutions.
The Application Layer Decoded: Beyond Protocol Management
Operating at Layer 7 of the OSI model, the application layer is often misunderstood as merely hosting apps like web browsers. In reality, it orchestrates three critical functions:
- Data Translation and Standardization
The layer converts raw data into formats recognizable by both humans and machines. For example:- SMTP (Simple Mail Transfer Protocol): Structures email text, attachments, and metadata into MIME (Multipurpose Internet Mail Extensions) formats.
- HTTP/HTTPS: Encodes web content into HTML/CSS for browsers and JSON/XML for APIs.
Without this translation, a JPEG image would appear as a meaningless string of hexadecimal values.
- User Authentication and Session Control
Before granting access, the application layer verifies identities via methods like OAuth 2.0 or SAML. During a Zoom call, it manages session persistence, ensuring you stay connected even if your IP changes mid-meeting. - Resource Negotiation
Ever noticed how Netflix adjusts video quality based on your internet speed? That’s the application layer’s Dynamic Adaptive Streaming over HTTP (DASH) at work, optimizing bandwidth usage in real time.
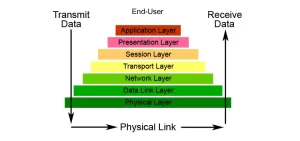
Real-World Applications: Where Theory Meets Practice
1. Healthcare Interoperability
HL7/FHIR standards at the application layer enable EHR systems from Epic and Cerner to share patient data securely. During the COVID-19 pandemic, these protocols allowed labs to transmit test results to global health agencies in standardized formats, accelerating response times.
2. Financial Transactions
When you tap a contactless card, the application layer’s EMV protocol:
- Encrypts payment details.
- Generates a one-time cryptogram to prevent fraud.
- Communicates with the bank’s server via ISO 8583 messaging.
3. Industrial IoT (IIoT)
MQTT (Message Queuing Telemetry Transport), an application layer protocol, enables sensors in a Siemens factory to publish temperature data to a central broker. Subscribed maintenance systems then analyze this data to predict equipment failures.
The Silent Enforcer: Security and Efficiency in Network Solutions
- API Gateways as Application Layer Firewalls
Modern solutions like Kong or Apigee embed security directly into the application layer:- Rate limiting to prevent DDoS attacks.
- JWT token validation for microservices.
- Data masking to hide sensitive fields in API responses.
A 2023 Gartner study found companies using these tools reduced API-related breaches by 67%.
- Latency Mitigation Through Caching
Content Delivery Networks (CDNs) like Cloudflare leverage the application layer to cache static resources closer to users. By storing copies of a website’s images in regional servers, page load times drop from 2.5 seconds to 300 milliseconds. - Legacy System Modernization
Mainframe-dependent industries (e.g., airlines) use application layer middleware like IBM MQ to transform COBOL-based reservation data into RESTful APIs, enabling integration with modern mobile apps.
The Future: AI and the Application Layer’s Evolution
Emerging trends are reshaping this layer’s capabilities:
- AI-Driven Protocol Optimization: GPT-4 models now dynamically adjust HTTP/3 parameters based on network congestion patterns, reducing video buffering by 40% in trials.
- Blockchain-Enhanced Authentication: Decentralized identifiers (DIDs) at the application layer let users control login credentials without centralized servers. Microsoft’s Entra ID already supports this for Azure services.
- Quantum-Safe Cryptography: Post-quantum algorithms like Kyber are being integrated into TLS 1.3 to future-proof application layer encryption.

Leave a comment