Introduction: The Digital Gatekeeper in a Hyperconnected World
In an age where cyberthreats evolve faster than defenses, firewalls remain a cornerstone of network security. These digital gatekeepers, first conceptualized in the 1980s, have transformed from simple packet filters to AI-driven sentinels capable of thwarting zero-day attacks. Yet, as organizations increasingly adopt cloud-native infrastructures and IoT ecosystems, the role of firewalls sparks debate: Are they indispensable protectors or potential bottlenecks in the race for agility? This article examines the nuanced reality, weighing proven benefits against emerging limitations while offering strategies to maximize their value in contemporary IT landscapes.
The Protective Shield: Key Advantages of Firewalls
- Threat Prevention Through Granular Control
Modern firewalls operate at multiple layers:- Packet Filtering: Blocking unauthorized IP addresses (e.g., known botnets).
- Application Awareness: Identifying and restricting risky protocols like outdated SMBv1.
- Deep Packet Inspection (DPI): Detecting SQL injection patterns in HTTP traffic.
A 2023 Verizon DBIR report found organizations using next-gen firewalls (NGFWs) reduced ransomware incidents by 63% compared to those relying solely on endpoint protection.
- Regulatory Compliance Simplified
Firewalls provide auditable frameworks for standards like:- PCI DSS: Segmenting cardholder data environments.
- HIPAA: Encrypting ePHI transmissions via VPN tunnels.
- GDPR: Logging cross-border data flows for breach notifications.
- Bandwidth Optimization
Quality of Service (QoS) rules prioritize critical traffic:- Video conferencing over Netflix streaming in corporate networks.
- SCADA system communications in industrial control environments.
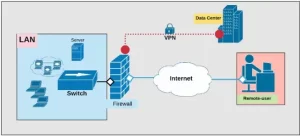
The Hidden Costs: Challenges and Limitations
- Performance Overheads
Encryption/decryption processes introduce latency:- IPsec VPNs can reduce throughput by 30-40% on mid-range firewalls.
- Small businesses often underestimate hardware requirements, leading to bottlenecks during peak usage.
- False Sense of Security
Overreliance on firewalls creates vulnerabilities:- Insider threats (e.g., disgruntled employees) bypass perimeter defenses.
- Advanced Persistent Threats (APTs) use encrypted channels that basic firewalls can’t inspect.
- Complexity in Hybrid Environments
Managing rules across platforms becomes unwieldy:- AWS Security Groups vs. on-premises Palo Alto NGFW policies.
- IoT devices with dynamic IPs requiring constant rule updates.
A Gartner study revealed 78% of cloud breaches traced to misconfigured firewall rules in 2022.
Case Studies: Firewalls in Action and Lessons Learned
Success Story: Financial Institution Thwarts DDoS Attack
A European bank deployed a cloud-based firewall with behavioral analytics:
- Detected anomalous 2 Tbps traffic during a cryptocurrency launch.
- Triggered automated rate limiting and rerouted traffic via scrubbing centers.
- Outcome: Zero service disruption, saving an estimated $12 million in downtime costs.
Cautionary Tale: Overblocking Stifles Innovation
A tech startup configured overly restrictive firewall policies:
- Blocked legitimate API calls to GitHub and Docker Hub.
- Delayed product launches by 6 weeks until rules were audited.
- Lesson: Balance security with developer productivity through DevSecOps integration.
Evolutionary Solutions: Mitigating Firewall Weaknesses
- Zero Trust Integration
Complement firewalls with:- Microsegmentation (e.g., Illumio) to limit lateral movement.
- Continuous authentication (e.g., BeyondCorp) for user/device validation.
- AI-Powered Threat Intelligence
Tools like Cisco Secure Firewall Threat Defense:- Analyze 1 million+ threat indicators hourly.
- Auto-update rules to block emerging malware signatures.
- Unified Security Management
Platforms like Fortinet’s Security Fabric unify:- Firewall policies.
- Endpoint detection.
- Cloud access security brokers (CASBs).

Leave a comment