Issue Description
MA5608T – Hardening how to harden our GPON configuration in a way that flooding (multicast, broadcast, icmp, dhcp etc.) from GPON to Network/Backbone could not happen
Customer had the issue that IPv6 DHCP requests from one of their customers flooded their network. Customer is connected with a ONT Huawei EG8245H (configured as bridge) to an OLT MA-5608T by using PPPoE as Data transport.
how to harden our GPON configuration in a way that flooding (multicast, broadcast, icmp, dhcp etc.) from GPON Customers to our Network/Backbone could not happen? Some kind of “ANTI DoS” Rules. Best practice configuration templates or ACL examples?
Our Customer traffic is in VLAN 60 and on interface gpon port 0/0/0
We’ve made this configuration:
display acl all
Total nonempty acl number is 1
Link ACL 4000, 3 rules
Acl’s step is 5
rule 3 permit type 0x8863 source 60
rule 2 permit type 0x8864 source 60
rule 1 deny
display acl ipv6 all
Total nonempty acl6 number is 1
Basic IPv6 ACL 2000, 1 rule
packet-filter inbound link-group 4000 port 0/0/0
packet-filter outbound link-group 4000 port 0/0/0
packet-filter inbound ipv6 ip-group 2000 port 0/0/0
packet-filter outbound ipv6 ip-group 2000 port 0/0/0
Handling Process
PRODUCT : MA5608T
VERSION : MA5600V800R015C10
If customer want to permit PPPOE packets though port 0/0/0, we had test it, it’s ok for packet-filter PPPOE packets and deny other packets.
if apply acl 4000 and acl 2000 at the same time. It will hit acl 4000 firstly. So the packet of ipv6 will drooped.
Solution
The packet’s though is based on ipv4 but your configuration ids based on ipv6. So the packet cannot hit the acl rules, if you want to deny IPv4 packets just use :
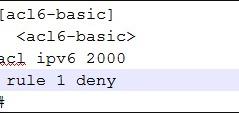
huawei(config-acl-basic-2000)#rule 1 deny
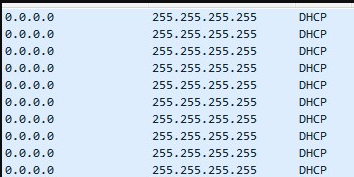
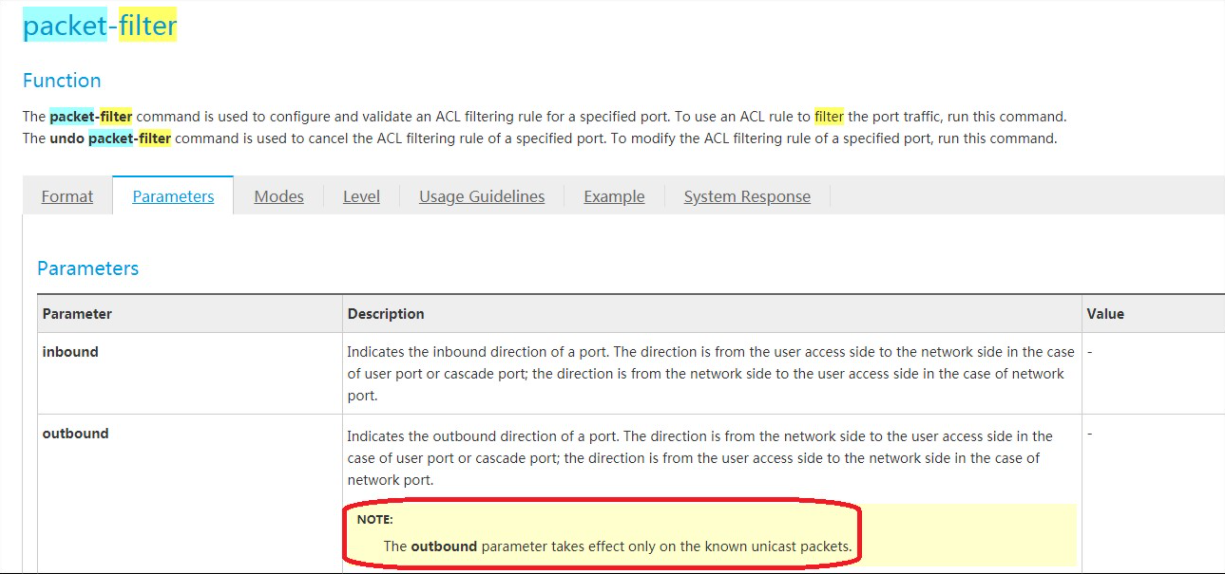
Please note that, the outbound parameter takes effect only on the known unicast packets. Therefore, some packets does not deny, maybe these packets are broadcast/multicast/unknown unicast packets on the outbound direction.
OUTBOUND
Indicates the outbound direction of a port. The direction is from the network side to the user access side in the case of user port or cascade port; the direction is from the user access side to the network side in the case of network port.
The outbound parameter takes effect only on the known unicast .
If only permit PPPoE packets pass, you can just configure the following configuration is enough.
packet-filter inbound link-group 4000 rule 1 port 0/0/0
packet-filter inbound link-group 4000 rule 2 port 0/0/0
packet-filter inbound link-group 4000 rule 3 port 0/0/0
packet-filter outbound link-group 4000 rule 1 port 0/0/0
packet-filter outbound link-group 4000 rule 2 port 0/0/0
packet-filter outbound link-group 4000 rule 3 port 0/0/0

Leave a comment